VPC Planning
Virtual Private Network VPC provides the ability to independently plan networks. How to use and how to plan your own network requires considering various factors such as business scenarios, future business changes, and business expansion.
Networks between different VPCs are isolated by default, but can be connected through the “VPC Communication” function to achieve intercommunication between different VPCs. There are many requirements for VPC segments during VPC communication, which is also a matter to be considered when planning a VPC. The following will introduce key points of VPC planning and restrictions of VPC communication to help users reasonably plan their own networks.
Suggestions on VPC Rules
If multiple projects, multiple regions, and multiple networks are involved, it is recommended to plan the network in advance when using VPC. Good network planning should have the following elements:
- The network segments between different VPCs do not overlap, which facilitates subsequent network communication.
- VPC and subnets should ensure sufficient network addresses while being not too large for future network expansion.
- The network segments of VPC and subnets are regular, making them easy for management and use.
- Use custom VPC.
When planning VPC networks, the following information is important:
(1) VPC and subnet network segments cannot be modified after being created. However,
- Custom VPCs support adding network segments (Note: Default VPC is no longer supported).
- If no subnet is under the VPC corresponding network segment, the VPC network segment can be deleted and rebuilt; for example, if the VPC contains two network segments, 192.168.0.0/16 and 10.0.0.0/16, and no subnet uses the 192.168.0.0/16 network segment, then the 192.168.0.0/16 network segment can be deleted within the VPC.
- If there are no resources in the subnet, the subnet can be deleted and rebuilt.
(2) There are following restrictions on subnets:
- The mask of the network segment must be at least /29.
- The 1st, 2nd, and last addresses in the subnet are reserved addresses, which are not available.
(3) Public service network segments cannot be used in VPC, and VPC network segments need to be larger than public service network segments. Check Public Service Network Segment.
VPC Scenario Examples
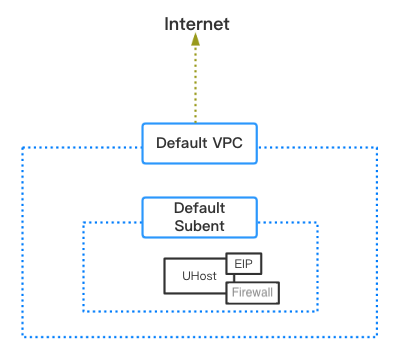
1. Single VPC with single subnet, for setting up simple web services or personal blogs.
In this scenario, there is no complex business isolation requirement, and no cross-domain intercommunication scenario. You can quickly create a cloud host by using custom VPC and custom subnet. By binding EIP, you can provide external access. To ensure the security of the cloud host, you can choose the default provided “Web Server Recommendation” firewall during the creation.
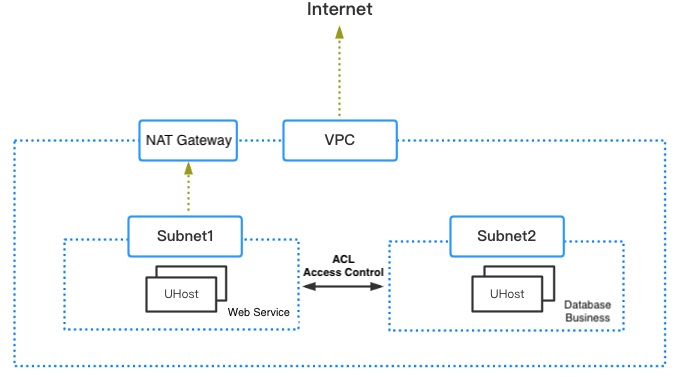
2. Single VPC with multiple subnets, achieving different business divisions.
In this scenario, all businesses are deployed in a single region on the cloud platform. In the VPC, different subnets are divided to achieve different business divisions. For example, subnet A provides external access for the Web business, subnet B has no external access to core databases, and subnet C simulates online business publishing in a pre-release environment.
The number of subnets depends on the specific business needs, and the size of the subnet can be determined by the number of hosts needed in each subnet. The mask in the subnet network segment determines how many cloud resource instances can be launched in the subnet, for example, if the subnet network segment is 192.168.1.0/24, and the mask is 24, except all 0, broadcast, and gateway addresses, the actual supported instance number is 256-3=253. Since the network segment cannot be modified after the subnet is created, the future scalability should be considered when considering the subnet’s mask.
After determining the number of subnets and subnet size, you can determine the size of the VPC network segment.
The networks between different subnets in the VPC are interconnected by default. If access rights need to be set for core database businesses, it can be configured through network ACLs. See ACL Planning Suggestions for details.
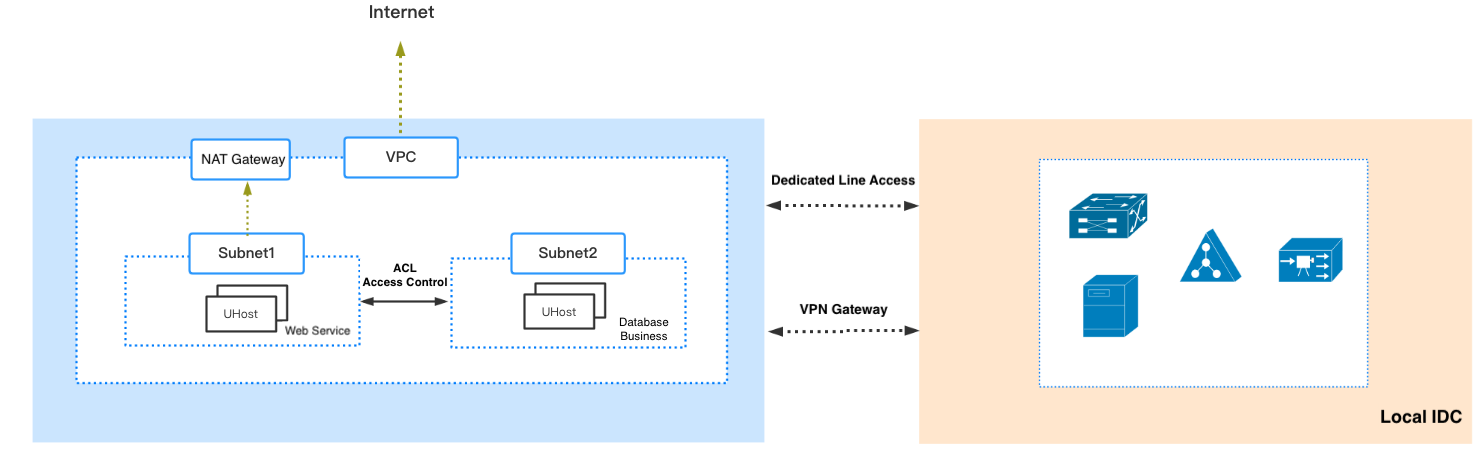
3. The cloud VPC is interconnected with the IDC machine room network to achieve smooth IDC expansion.
In this scenario, the user’s business is distributed on the cloud platform and their own IDC machine room, and can achieve smooth cloudification of the IDC, using the elasticity of the cloud platform to promptly respond to sudden business needs.
There are two ways to connect the cloud VPC and the IDC machine room, direct line access or IPSec VPN. Direct line access is a method of connecting the local IDC to the Surfercloud data center via a dedicated line. After access, the local IDC will be virtualized into a VPC on the cloud, only needing to connect with the cloud VPC to achieve intercommunication. VPN gateway is based on the Internet, and intercommunication between the cloud network VPC and the local IDC can be achieved through an encrypted data transmission tunnel.
Both methods require that the network segments of the cloud VPC and the local IDC do not overlap. Therefore, when deploying businesses in the cloud, you need to choose unused network segments of the local IDC when planning the VPC.
VPC Communication Rules
1. Name Explanation
- Custom Network Segment: Standard network segment. At present, all actively created VPCs belong to this type. Due to historical reasons, some customer’s VPC may contain both default and custom network segments.
- Default VPC: Automatically created by the system, VPC with default network segment.
The default VPC does not support adding network segments and no longer provides default VPC.
- Custom VPC: VPC with all its network segments being customized.
2. Communication Restrictions
(1) Same region: default network segments can overlap (IP can not conflict), while custom network segments can’t overlap. See the table below:
| This end\Other end | Default VPC with only default network segment | Custom VPC with only custom network segment | Default VPC with custom network segment |
|---|---|---|---|
| Default VPC with only default network segment | Default VPC will not be provided in the future, and it will no longer support interconnection with Default VPC | If the network segment is the same, communication is forbidden; If it is the same as the custom network segment that has been interconnected, communication is forbidden | If it is the same as the custom network segment that has been interconnected, communication is forbidden |
| Custom VPC with only custom network segment | If the network segment is the same, communication is forbidden; If it is the same as the custom network segment that has been interconnected, communication is forbidden | If the network segment is the same, communication is forbidden; If it is the same as the custom network segment that has been interconnected, communication is forbidden | |
| Default VPC with custom network segment | Default VPC will not be provided in the future, and it will no longer support interconnection with Default VPC | If the custom network segment is the same, communication is forbidden; If the custom network segment is the same as the interconnected network segment, communication is forbidden |
3. Communication Principles
- When two VPCs are connected, the system will add the routing rules of the connected peer VPC network segment to the two VPC’s routing tables respectively.
- For the default network segment in the peer VPC, the local VPC adds Local type routes.
- For the custom network segment in the peer VPC, the local VPC adds VNet routes.
For routing table related terms, see [Routing Table](/docs/vpc/introduction/routetable#Route Rule Type Routing table rule’s next hop type enumeration is as follows:), and the communication principles are explained in detail through examples below.
Example 1: Connection between Custom VPCs
When the local network segment is the same as the peer network segment, communication is forbidden; if the peer network segment contains the custom network segment that the local VPC has been interconnected with, communication is forbidden.
vpc_a, vpc_b, vpc_c are all custom VPCs with only custom network segments.
vpc_a can connect to vpc_b. The two VPCs do not contain the same network segment, and there is no route that contains the same target network segment as the peer network segment among the existing routing rules.
vpc_b is forbidden to connect to vpc_c, because they contain the same “custom network segment 3”. If communication is allowed, when vpc_b internal machines access “custom network segment 3”, the forwarding plane cannot judge whether to send it to the local VPC or the peer’s vpc_c.
If vpc_a has already been connected to vpc_b, it is forbidden to be connected to vpc_c, because they contain the same “custom network segment 1”, and vpc_a has been connected with the same “custom network segment 3” in vpc_b.